Microsoft Defender: manage and protect your company’s remote computers and services

Implementing the right cybersecurity strategy requires a delicate balance between protection and convenience. In the world of computer security, the trend is convenience with the purpose of business operability and efficiency. In this sense, Microsoft Defender favors shielding against all types of threats.
What is Microsoft Defender
Microsoft changed the names of some security solutions and merged them under the name Defender. With these changes, the company wants to create more clarity in its offering and make it easier to understand all of Microsoft’s security capabilities.
Defender offers a unified set of security solutions that, thanks to XDR (Extended detection and response) technology, monitor different domains: identities, endpoints, cloud applications, email and documents. XDR stands for Extended Detection and Response and is a new approach designed to deliver intelligent, automated, integrated security and responsiveness in a centralized manner.

Microsoft Defender Security Center.
And it is no longer enough to protect only separate domains. Cyberattacks occur in several domains at the same time and spread laterally within organizations. XDR makes it possible to connect different alerts that are seemingly inconsistent and therefore outwit attackers.
Suite of security solutions
Some of the solutions that make up Defender are:
- Microsoft 365 Defender uses AI to intercept attacks in an automated and cross-domain manner. With dashboards and reports, it provides a clear view of which threats are active and where.
- Microsoft Defender for Endpoint is relevant, among other things, for the growing number of devices being used to work remotely. These are well covered with this solution that offers preventative and post-breach functionalities. Microsoft Defender for Endpoints continually investigates the security posture of enterprise devices for potential breaches.
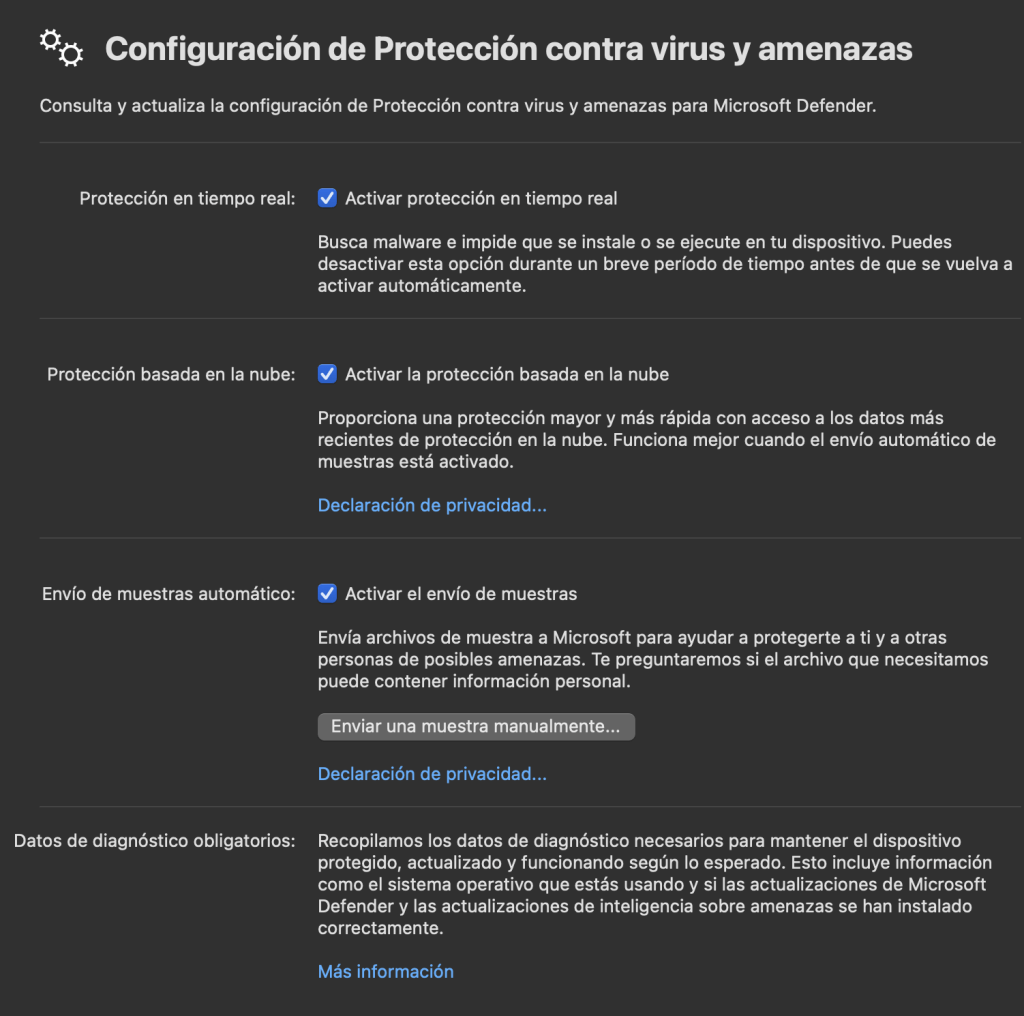
Microsoft Defender for Endpoint on a MAC.
- Microsoft Defender for Office 365 protects all Office 365 applications from advanced threats. For example, phishing and email fraud, as well as breaches through corrupted documents and collaboration tools.
- Microsoft Defender for Identity manages identity risks. Identity theft, in which cybercriminals gain access to sensitive or valuable data, is a common practice. Therefore, proper management and control of identities are crucial for a secure working environment. Microsoft Defender for Identity takes this to the next level by correlating suspicious signals with other alerts and facilitating secure access for employees.
- Microsoft Intune provides centralized enterprise mobility management (EMM) in the cloud. More and more employees are shifting their tasks to the mobile plane. Well, Intune allows the analysis of security risks in mobile devices and applications from a single control panel.
What are the benefits of Microsoft Defender
Let’s see what are the main advantageous features that this suite of solutions brings to organizations.
Real-time protection
Real-time protection is a component of the behavioral containment and blocking capabilities in Microsoft Defender for Endpoint. When Microsoft Defender Antivirus detects suspicious behavior or file, the information is sent to multiple classifiers. The fast loop protection engine inspects and correlates information with other signals to reach a decision on whether to lock a file.
Verification and classification is done quickly. It results in a rapid blocking of confirmed malware and drives protection across the ecosystem. With feedback loop locking, your organization’s devices are better protected against attacks.
Network Protection
Network protection allows or blocks specific URLs and IP addresses, either manually or through threat intelligence sources. Helps prevent applications from accessing malicious domains. This feature is available but will not work without our antivirus capabilities enabled. Detailed information about network protection events and blocks can be viewed and analyzed in the Microsoft Defender Security Center, where security teams can also run advanced search queries for a more proactive approach to security.
Blocking at first sight
This feature provides a way to detect and block new malware in a short period of time. When Microsoft Defender Antivirus finds a file with suspicious characteristics that has not been identified, check out our cloud protection backend . Heuristics, machine learning , and automatic file analysis are used to determine if files are malicious and not a threat. This feature and its required settings are enabled by default when certain prerequisite settings are opened, but they will not work without Microsoft Defender Antivirus.
Detection and blocking of potentially unwanted applications
Potentially unwanted applications do not have the status of viruses, among other threats. However, they adversely affect the performance of the devices. These kinds of applications can also include programs that have a bad reputation. Microsoft Defender for Endpoint identifies and evaluates these apps for certain types of unwanted behavior.
Detailed information about blocked malware
When Microsoft Defender Antivirus locks a file, the alert, computer risk assessment, and actions taken across the organization are logged. This provides accountability and traceability. The ability to allow or block a file directly from Microsoft Defender for Endpoint is available. It also includes the ability to request a download or collect the file. If a third-party solution blocks malware, the organization has much less visibility and fewer reactive actions available.
Compliance and geographic location
The components within Microsoft Defender and the geographic location of the data comply with the same ISO 27001 standard. When we use the Defender for Endpoint platform, we obtain data related to geographic sovereignty, ISO compliance, and data retention. We can avoid the potential risk of employing a third-party vendor with a different level of compliance or the task of validating compliance with the third-party vendor.
In short, Microsoft Defender is a multi-component security solution that can fit the needs of organizations of all sizes.
Endpoint Manager, Microsoft Defender, Microsoft Defender for Identity, Microsoft Defender for Office 365, Microsoft Intune
Go back



